Today I experienced an interesting story with my Mikrotik router at home. While updating the PiHole instance the system hat quite some problems obtaining either system updates but also the PiHole update packages. A ping on 9.9.9.9 showed that the Raspberry – on which the PiHole was hosted – had somewhat between 70-80% packet loss. Pinging the same IP from a Windows machine resulted in 0% packet.
All this happened only on wired connections but did not cause any problmes when connected via wifi.
As the Raspberry is directly attached to the Mikrotik router I also tried to connect it via a switch in between as that’s the setup for the windows machine. Same behavior.
Running pings from 3 Linux systems in the network and two Windows systems (even with exchanging network connections to be directly connected to the Mikrotik and connecting through the switch) came up with an interesting result:
All Windows machines had hardly any packet loss in 10 mins (<3%) and all the Linux systems had somewhat between 70%-80% packet loss (tested with a ping).
Any ping that involved the Mikrotik routers L2 functionality seemed to result in packet loss on the Linux machines.
Pinging any other machine on the same subnet worked without problems, but as soon as there was one hob in between the problem occurred.
Interestingly the problem vanished as far as the Torch tool was activated and no more packet loss occurred on any of the systems.
After some additional troubleshooting time (and disabling nearly all Mikrotik-configuration -> Firewall-Rules/Interfaces) the problem seemed to be with the Bridge interface used. It seems that the deactivation of the IP Firewall for the bridge interface caused the problem. After enabling it the behavior vanished and all systems no longer had any packet loss issues.
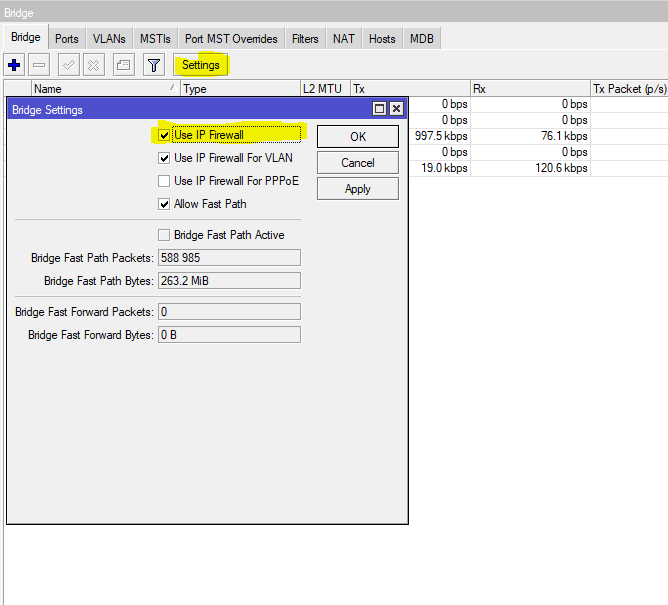
[admin@MikroTik] /interface bridge settings> /interface bridge settings
[admin@MikroTik] /interface bridge settings> set use-ip-firewall yes