It took me quite some troubleshooting time, but in the end it’s a quite interessting conclusion.
After trying to create a scheduled task that runs every second Saturday per month, I ran into the following error:
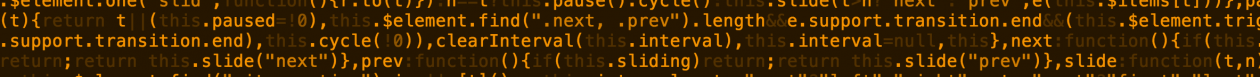
Set-ScheduledTask : The parameter is incorrect.
At C:\ITX\itxWindowsUpdate.ps1:436 char:5
+ Set-ScheduledTask -InputObject $task -User $(Get-LocalUser -Name ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidArgument: (PS_ScheduledTask:Root/Microsoft/...S_ScheduledTask) [Set-ScheduledTask], CimException
+ FullyQualifiedErrorId : HRESULT 0x80070057,Set-ScheduledTaskAs Windows Powershell is not able to create monthly tasks I used schtasks.exe utility to create the skeleton for the task/minimal task containing the trigger-definition and afterwards manipulate it via powershell to add the missing configuration.
To do so i used Get-ScheduledTask to obtaint he object references for the task and Set-ScheduledTask to write the object again.
Turns out – the task obtained via Get-ScheduledTask contains the trigger defintion for the montly repetition which can’t be handled by powershell and therefor the task itself can not be saved again but results in the above error. 😜
As it seems there are only two ways on how to deal with that problem:
Export the task-definition as an XML and just reimport it via powershell on other systems which require the same configuration (currently untested) or run it daily and deal with the problem within the script.
Lil bit of the debugging-code as a reference for future projects.
Write-Host -ForegroundColor Yellow "Modifying the task"
$action=New-ScheduledTaskAction -Execute "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Argument '-NoProfile -command "& C:\BLUB\WindowsUpdate\WindowsUpdate.ps1 -reboot_machine 0"'
$principal = New-ScheduledTaskPrincipal -LogonType Password -RunLevel Highest -UserId "$($env:COMPUTERNAME)\Administrator"
#$principal = New-ScheduledTaskPrincipal -RunLevel Highest -UserId "$($env:COMPUTERNAME)\Administrator"
#$task=New-ScheduledTask -Action $action -Description "Daily Update Task for Monitoring and Defender Updates" -Trigger $trigger -Settings $settings -Principal $
$task=$(Get-ScheduledTask -TaskName $task_name -TaskPath \BLUB\)
#$task.Actions=$action
$task.Description="TEST_test"
#$task.Principal=$principal
#Register-ScheduledTask -TaskName $task_name -InputObject $task -TaskPath BLUB -User $(Get-LocalUser -Name Administrator) -Password $password
$task | Set-ScheduledTask -User $(Get-LocalUser -Name Administrator) -Password $password
#-User $(Get-LocalUser -Name Administrator) -Password $password
#Set-ScheduledTask -TaskPath "BLUB" -TaskName $task_name -Action $action -Principal $principal
#-Principal $principal
# -User $(Get-LocalUser -Name Administrator)