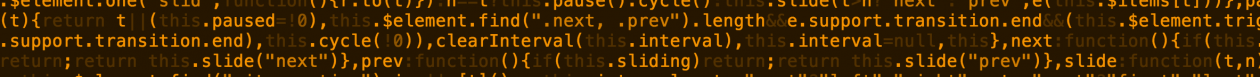
When trying to interact with the Zabbix-API via Powershell one might run into the problem, that an API request will not be executed successfully, but an error similar to the following one, will be displayed:
code message data
---- ------- ----
-32602 Invalid params. Invalid parameter "/1/filter/conditions": an array is expected.Especially when using some code like in the below snippet which uses @(…) and @{…} to define data via arrays and hashtables:
function ZbxUpdateTestAction
{
$params = @{
body = @{
"jsonrpc"= "2.0"
"method"= "action.update"
"params"= @{
"actionid" = "117"
"status" = 0
"filter" = @{
"evaltype" = 0
"conditions" = @(
@{
"conditiontype" = 4
"operator" = 5
"value"= 3
}
@{
"conditiontype" = 0
"operator" = 0
"value"= 435
}
)
}
}
"id"= 1
"auth" = "$api_token"
} | ConvertTo-Json
uri = $zbx_api_uri
headers = @{
"Content-Type" = "application/json"
"Authorization" = "Bearer $api_token"
}
method = "Post"
}
$result = Invoke-WebRequest @params
return $result.Content | ConvertFrom-Json
}The above snippet just shows a test function to manually update an action and set conditions to send out alerts for severities of warning or higher for a specific host group.
However – when executed it will fail with the error from snippet 1.
This is because Powershell does the JSON-conversion only to a certain depth. If your structure reaches a deeper level, it will simply stop converting the dict or array which results in the above error.
Troubleshooting it, could be quite a pain in the ass as it’s not that simple to spot and when gradually extending the object it just works fine till you exceed a depth of 2.
To fix this – simple specify the depth for ConvertTo-Json
e.g.
function ZbxUpdateTestAction
{
$params = @{
body = @{
"jsonrpc"= "2.0"
"method"= "action.update"
"params"= @{
"actionid" = "117"
"status" = 0
"filter" = @{
"evaltype" = 0
"conditions" = @(
@{
"conditiontype" = 4
"operator" = 5
"value"= 3
}
@{
"conditiontype" = 0
"operator" = 0
"value"= 435
}
)
}
}
"id"= 1
"auth" = "$api_token"
} | ConvertTo-Json -Depth 5
uri = $zbx_api_uri
headers = @{
"Content-Type" = "application/json"
"Authorization" = "Bearer $api_token"
}
method = "Post"
}
$result = Invoke-WebRequest @params
return $result.Content | ConvertFrom-Json
}Compare line 29 between the two snippets